User Accounts Overview
Journey Manager (JM) The transaction engine for the platform. | System Manager / DevOps | 19.05 This feature was updated in 19.05.
Journey Manager defines user accounts to authenticate and authorize users to log on to the Journey Manager Home Dashboard and one or more form spaces. to access assigned tasks, or Workspaces. This is controlled by assigning users to form spaces, where the Manager dashboard is one of form spaces.
There are two types of the users that can access forms:
- Authenticated users
- Anonymous users (unauthenticated or public users)
For more information, see Authenticated vs Unauthenticated Transactions.
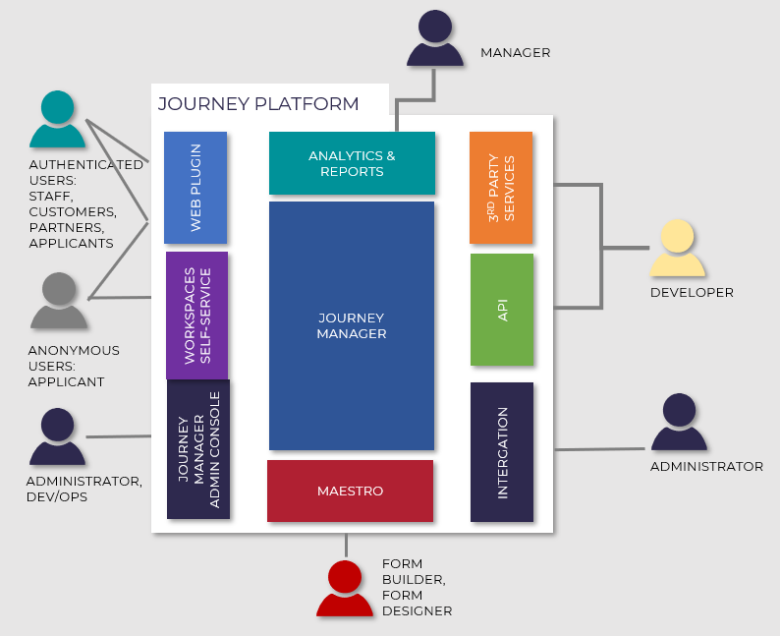
The diagram below illustrates various user types and what they can access in the Temenos Journey Manager.
Each user account can belong to one or more roles. Roles are collections of user accounts with similar access rights. Similarly, user accounts can belong to any number of groups, which group user accounts into non-permission based collections, for example, administrators who are interested in receiving certain email notifications.
An administrator is a user account that is associated with the Manager dashboard form space. A form space user is a user account that is associated with at least one form space. Note that these categories are not mutually exclusive: An administrator can also be associated with arbitrarily form spaces, and can have global access or be restricted to data associated with one or more specific organizations.
Manager controls access to certain content or actions using permissions. When requesting restricted content, Manager only allows this if the required permissions are present. Permissions can be granted to one or more roles, and a role is characterized by the permissions it contains. If a user account belongs to several roles, they have all permissions that are set for at least one of their roles.
As users make changes to Manager's configuration, these changes are tracked and written to the audit log. This makes it possible to view an object's history and review a specific user's changes.
A user account is part of the Journey Manager security management system, which allows for fine-grained control based on user's functions, roles, groups, and access permissions. To provide flexibility around the security configuration, Manager supports one or multiple security managers. A security manager contains such settings as how users are authenticated, lockout and password settings, session timeout, SSO configuration and user self-registration settings.
Each security manager contains one or more authentication managers responsible for authenticating a user during login. Each form space can be associated with its own security manager or use the default security manager defined in the system.
Manager provides the easy-to-use interface to create, modify, and deactivate user accounts, as well as manage access permissions, user roles and groups. It also comes with the bulk import functionality to create multiple users, including user's details, roles, groups and access configurations, which significantly simplifies user provisioning task.
Manager doesn't impose any limits on the number of user accounts you can have. However, as customersA customer is a person who uses Temenos Journey Manager to create, host and manage application forms. Other names for a customer is a client. handle user authentication in different ways, there might be some limit in the Security Managers the customers use, such as SSO, LDAP and so on, or a physical limit in the database. Most customers only authenticate their own users, but some might also authenticate form applicants raising transactions. In this case, they could theoretically have thousands of users.
Manager doesn't have any built-in functionality to purge old or inactive user accounts automatically, so you should periodically audit user accounts to ensure their number doesn't grow beyond a point that impedes the system performance. For more information, see data retention management.
Authenticated Users
Before users can log in to a form space, which requires authentication, they must have valid user accounts. Manager allows an administrator to create a user and grants access to one or more form spaces. The user receives an email with login credentials, such as a username and password, to access forms hosted on the form space.
Manager allows authenticated users to login to a form pace using credentials by delegating authentication and authorization to the 3rd party system, such as Active Directory, LDAPLightweight Directory Access Protocol (LDAP) is an open, vendor-neutral, industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol network. or SSOSingle sign-on (SSO) is a property of access control of multiple related, yet independent, software systems. With this property, a user logs in with a single ID and password to gain access to any of several related systems.. Manager can also maintain local users, such as contractors that are not in the organization's LDAP system.
The authenticated users can be:
- Business users internal to a company
- Government departments
- Staff and contractors that work in the field
Authenticated users have access to the advance features of the secured portal such as Form, Task and History pages.
Anonymous Users
Anonymous (unauthenticated or public) users can access forms if its form space is configured to allow anonymous access. An example of such a form space is the Web Plug-in form space. Members of the public click on a link from a company website which opens an unsecured form page in the portal. The available list of forms is manually maintained by the company on their website.
Using anonymous users has the following advantages:
- Removes the overhead of maintaining users and passwords.
- Minimizes privacy issues related with storing public users' data, such as PIIPersonally Identifiable Information (PII) is information about an individual that can be used to distinguish or trace an individual‘s identity, such as name, social security number, date and place of birth, mother‘s maiden name, or biometric records; and any other information that is linked to an individual. In Europe, PII is known as personal data..
Anonymous users don't have access to the advance features of the secured portal such as Form, Task and History pages.
An anonymous user can still use the forms, but with the following limitations:
- If they save a form, an email will be sent to them with a link that will open the saved form.
- Tasks are emailed to a user with a link to open the task.
- Job statuses can be emailed out the user as the job progresses.
Anonymous users must provide their email address. Optionally, a security question can be set to open saved forms and tasks.
You can grant standard roles to users to control their access to and define capabilities at their form spaces. Each form space has a set of roles that can be granted to a user. You can also create a new role as needed.
A typical form user must only be granted access to a form space where forms are hosted. This allows self-registered users immediate access to forms. However, most users must be granted access to:
Quite often you may want to restrict user's access to a limited number of forms or even one form that are hosted on a form space. You can achieve this by creating a form group, adding a user to that group and assigning that group to a form you want to restrict an access to. Alternatively, you can create a special form space, assign the form to this form space and then assign this form space to that user. For more information, see how to provision a user account.
When working with user accounts, you should consider the environment that users are accessing, which can be production, development, or testing environment. Manager is designed to be customizable to accommodate enterprise’s security configurations and policies. The following users require access to a production environment:
- Form users to access, complete and submit forms.
- Operational staff to monitor and manage transactions and collaboration jobs.
- Administrators to manage the environment and keep it secure.
- System managers to view and analyze transaction reports.
- Reviewer or manager to approve or reject customer form applications.
The following users require access to a development and test environments:
- Administrators to manage the environment and keep it secure.
- Form builders to create and configure forms.
- Testers to test forms.
Users can only log into a form space if their user accounts are assigned to that form space. It is not possible to assign a form space to a user account when the form space is only accessed anonymously.
The following users should have access to form spaces:
- Form users to log into a form space.
- Form Builders to log into one or more form spaces:
- Maestro
- Manager
- Journey Analytics
- Business Reports
- Salesforce
- Workspaces
- Administrators to log into Manager.
- Testers to log into various form spaces.
- Operators to log into Manager.
- Managers to log into one or more form spaces:
- Journey Analytics
- Business Reports
- Salesforce
- Workspaces
A standard user account contains the following information:
- Credentials - username and password
- User type - security managers used in your form space, which can be Local, LDAP or SSO
- User profiles - user contact details. A user can have more than one user profile containing different contact details
- Form spaces - assigned to the user to authorize access to specific form spaces
- Organizations - assigned to the user to authorize access to specific organizations. Applies to modules, but not relevant for form spaces
- Roles - grants individual roles which specify fine-grained permissions to access Temenos Journey Manager platform and form spaces
- Groups - belongs to an individual group for authorizing access to restricted forms, receive alerts and notifications pertaining to a group
Manager enforces some extra security rules to ensure that users cannot access restricted content, such as organizations, groups, users, forms, transactions and collaboration jobs. | 19.05 This feature was introduced in 19.05.
Next, learn how to view user accounts.