Form Submission Access Controller Service
Journey Manager (JM) The transaction engine for the platform. | System Manager / DevOps | All versions This feature is related to all versions.
Manager has a variety of built-in security access rules. One of them is to allow a user to access form's submissions only if a user's session matches a session used to render that form. If the sessions don't match, the user is expected to re-enter the save challenge details.
Composer forms prior to version 4.3 SP3 don't have this functionality within the form flow.
Manager comes with the form submission access controller service, which you can use to change (override) the existing users access rules to form's submissions.
If a session is re-established, access to the submissions will only be valid within the Anonymous Submission Access Timeout time configured for this form space.
To configure the form submission access controller service:
- Select Services > Core Global Services.
- Locate the service and click Edit.
- Click the Service Definition tab to edit the standard service configuration.
- Click the Parameters Edit tab to view or update the service configuration.
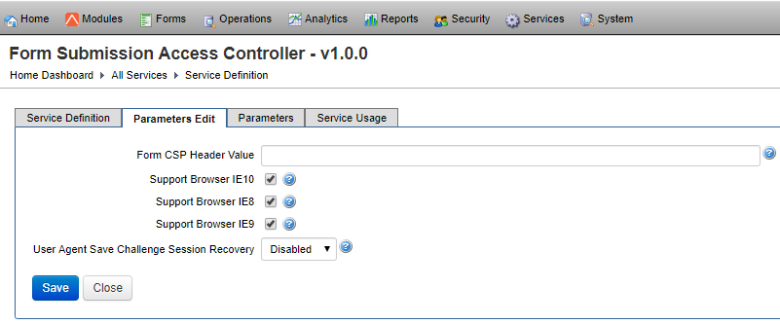
- Specify the system wide Content Security PolicyContent Security Policy (CSP) is a computer security standard introduced to prevent cross-site scripting (XSS), clickjacking and other code injection attacks resulting from execution of malicious content in the trusted web page context. CSP provides a standard method for website owners to declare approved origins of content that browsers should be allowed to load on that website—covered types are JavaScript, CSS, HTML frames, web workers, fonts, images, embeddable objects such as Java applets, ActiveX, audio and video files, and other HTML5 features. For more information, see https://www.w3.org/TR/CSP/ (CSP) security HTTP header value in the Form CSP Header Value field.
Note Check the CORS Headers setting of your form space and the System Default CSP Header setting of your organization to ensure the correct CSP is used.
- Select the Support Browser IE10 checkbox to support the legacy Internet Explorer 10 (IE10) browser.
- Select the Support Browser IE8 checkbox to support the legacy Internet Explorer 8 (IE8) browser.
- Select the Support Browser IE9 checkbox to support the legacy Internet Explorer 9 (IE9) browser.
Note IE8, 9 and 10 don't support TLS 1.1-1.2 or Content Security Protection (CSP).
- Select a save challenge session recovery mode from the User Agent Save Challenge Session Recovery dropdown list to override the existing behavior. You can use one of the following options:
- Disabled: sessions aren't re-establish, so users must re-enter the save challenge details to recover sessions. This is the default option.
- Enabled: user agentUser agent is software (a software agent) that is acting on behalf of a user. One common use of the term refers to a web browser that retrieves, renders and facilitates end user interaction with Web content. check is enabled to allow sessions to be re-established.
- 4.3.0SP2: user agentUser agent is software (a software agent) that is acting on behalf of a user. One common use of the term refers to a web browser that retrieves, renders and facilitates end user interaction with Web content. check is enabled to allow sessions to be re-established for forms built using Composer version 4.3 SP2 and higher.
- Click Save to update the changes.
Next, learn how to view core global services.