AWS STS Service Connection
Journey Manager (JM) The transaction engine for the platform. | System Manager / DevOps | All versions This feature is related to all versions.
Manager allows you to create and configure a AWS STSThe AWS Security Token Service (STS) is a web service that enables you to request temporary, limited-privilege credentials for AWS Identity and Access Management (IAM) users or for users that you authenticate (federated users). service connection to be used in the AWS SQS System Event Publisher services, which publish events to the various queues using the AWS STS protocol.
To configure a service connection:
- Select Services > Service Connections.
- Locate an Amazon STS service connection or click New to create a new service connection.
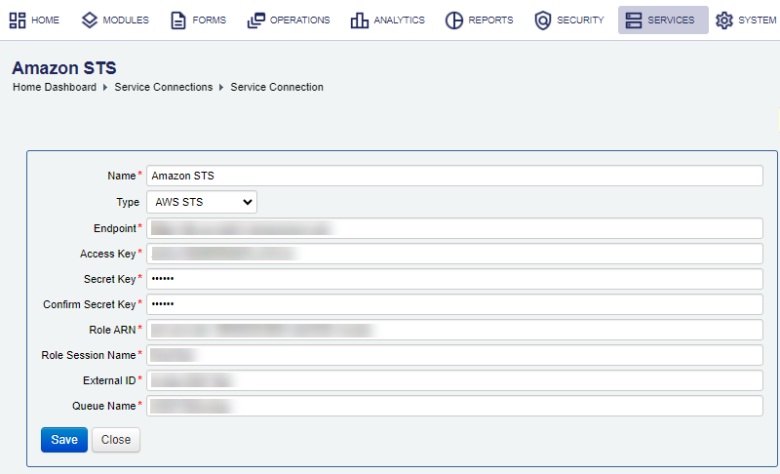
- Provide a unique service connection name in the Name field.
- Select the AWS STS type from the Type dropdown list.
- Enter the Endpoint as a URL for the AWS STS queue service, for example,
https://sts.my-domain.com. - Provide the Access Key, which is an AWS access key ID. You use access keys to sign programmatic requests that you make to AWS if you use AWS CLI commands or using AWS API operations. You must use both the access key and secret access key together to authenticate your requests. For more information, see AWS documentation.
- Provide the Secret Key.
- Confirm the Secret Key in the Confirm Secret Key field.
- Provide the Role ARNAn Amazon Resource Name (ARN) is a file naming convention used to identify a particular resource in the Amazon Web Services (AWS) public cloud. ARNs, which are specific to AWS, help an administrator track and use AWS items and policies across AWS products and API calls. , which is the Amazon Resource Name (ARN) of the role to assume.
- Enter the Role Session Name, which is an identifier for the assumed role session. Use the role session name to uniquely identify a session when the same role is assumed by different principals or for different reasons. In cross-account scenarios, the role session name is visible to, and can be logged by the account that owns the role. For example,
MyRoleTest. - Provide the External ID. A unique identifier that might be required when you assume a role in another account. If the administrator of the account to which the role belongs provided you with an external ID, then provide that value in the ExternalId parameter. This value can be any string, such as a passphrase or account number. Because a cross-account role is usually set up to trust everyone in an account, the administrator of the trusting account might send an external ID to the administrator of the trusted account. For more information, see AWS documentation.
- Enter the Queue Name configured at the endpoint URL, for example,
my-sts-queue. - Click Save to update the changes.
Next, learn about other service connection types.